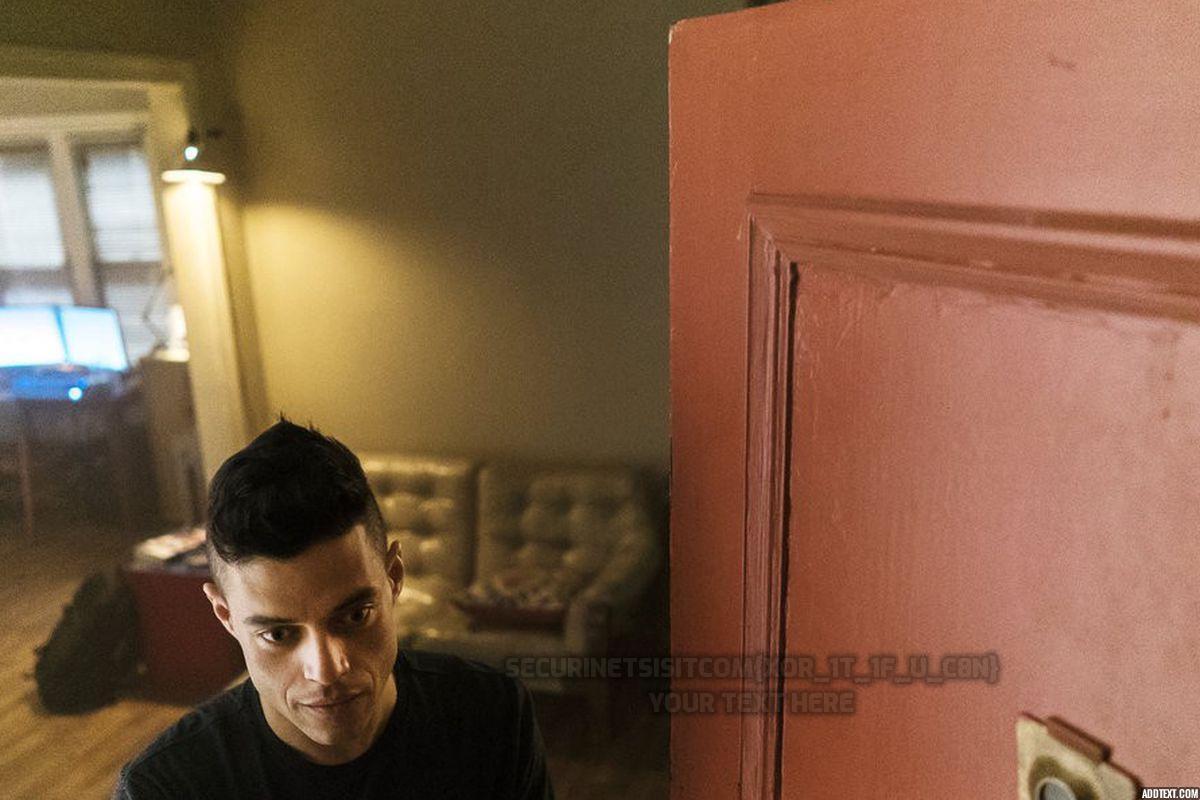CTF Writeup: ISITCOM Friendly CTF
Welcome to the write-ups for the Cryptography challenges from the SECURINETS ISITCOM Friendly CTF !
Intro
As the author of these tasks, I set out to create engaging and educational challenges designed to test your crypto knowledge in fun and practical ways.
In this post, I’ll walk you through the solutions for the six challenges I designed — covering topics like:
- 🔑 Hash cracking
- 🔐 XOR encryption
- 🔓 Weaknesses in RSA
Each challenge was built to teach something new while giving players a real-world look into how cryptographic flaws are exploited.
Whether you’re revisiting the CTF to reinforce what you learned, or you’re exploring these for the first time, I hope you find these write-ups both helpful and beginner-friendly.
Description
Let’s dive into the solutions and explore the thinking behind each challenge!
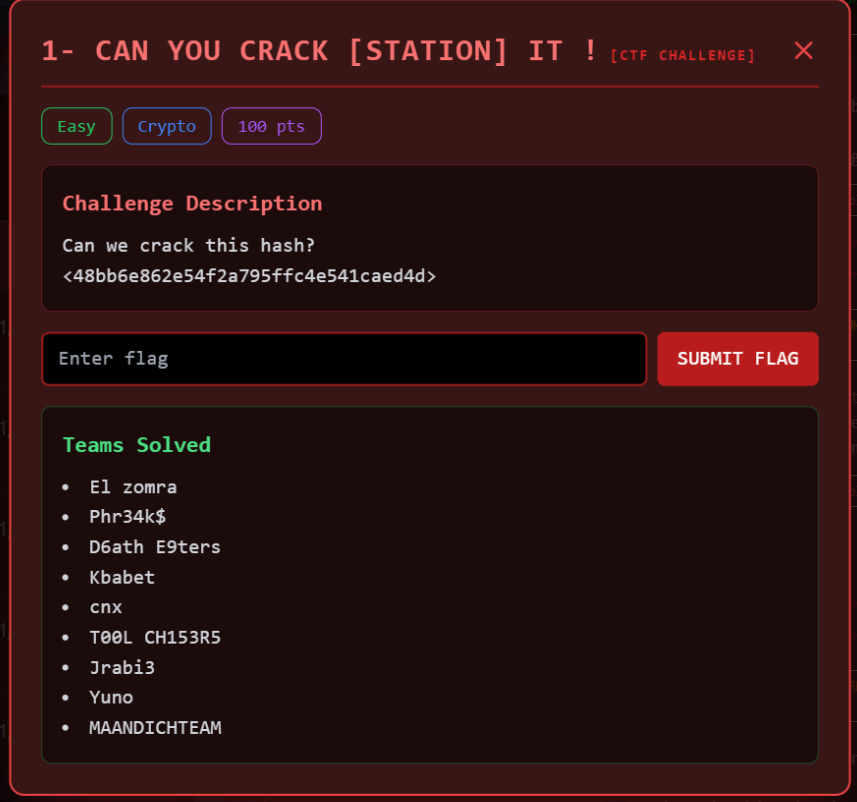
Task 1:
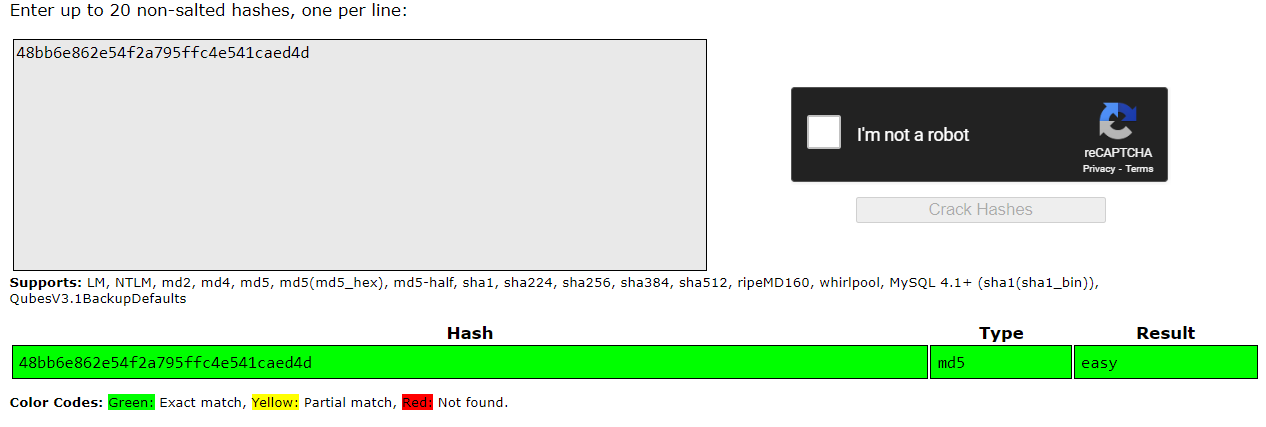
Solution: This task is straightforward, as the name indicates. Let’s search for “crack station” on Google, where we found a website to crack the hash crackstation
and here we have our flag!
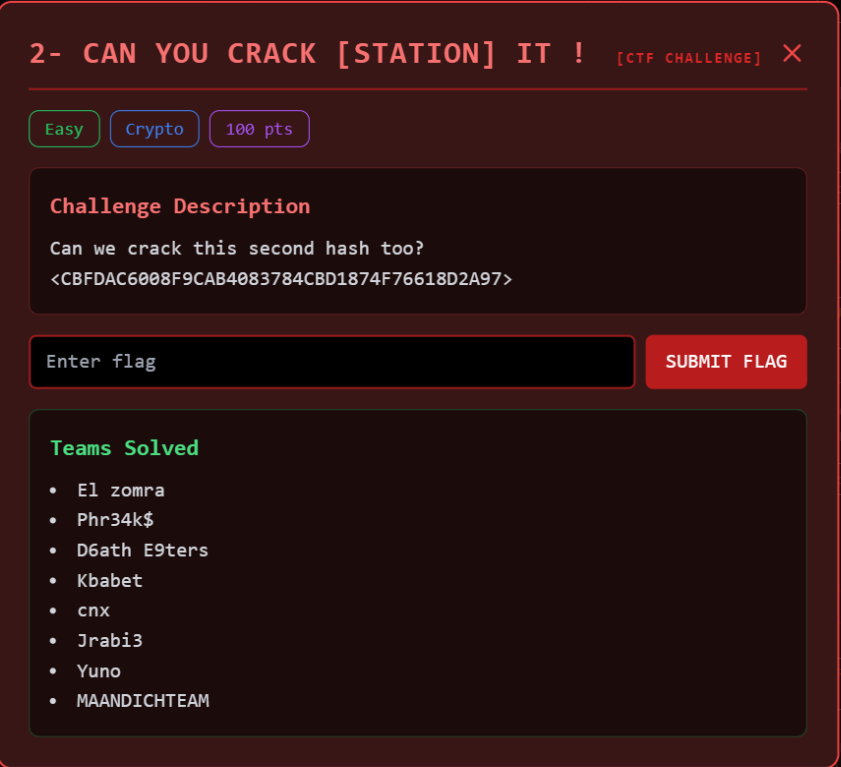
Task 2:
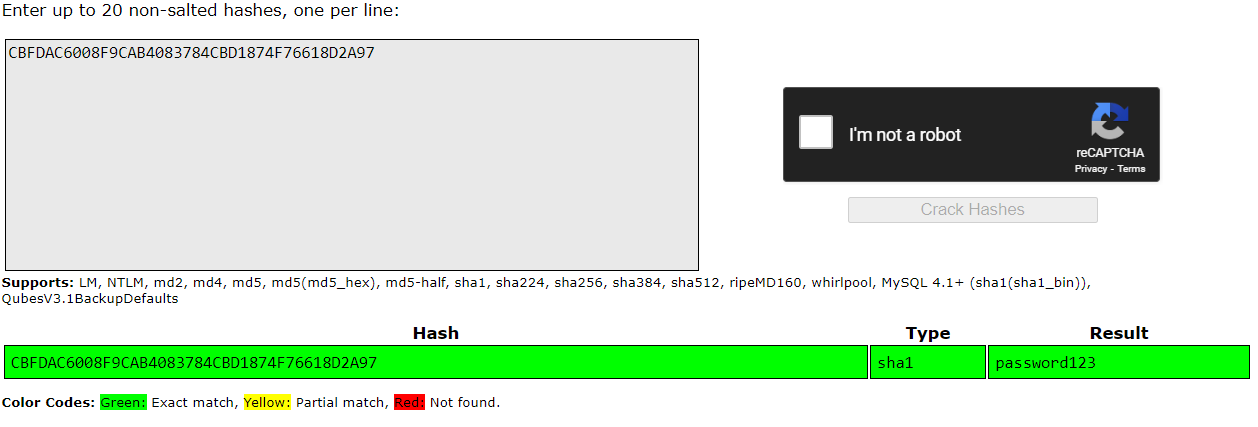
Solution: Let’s check crackstation too for this hash:
and here we have our flag!
Task 3:
I uploaded this encrypted flag for the challenge, so take a look!
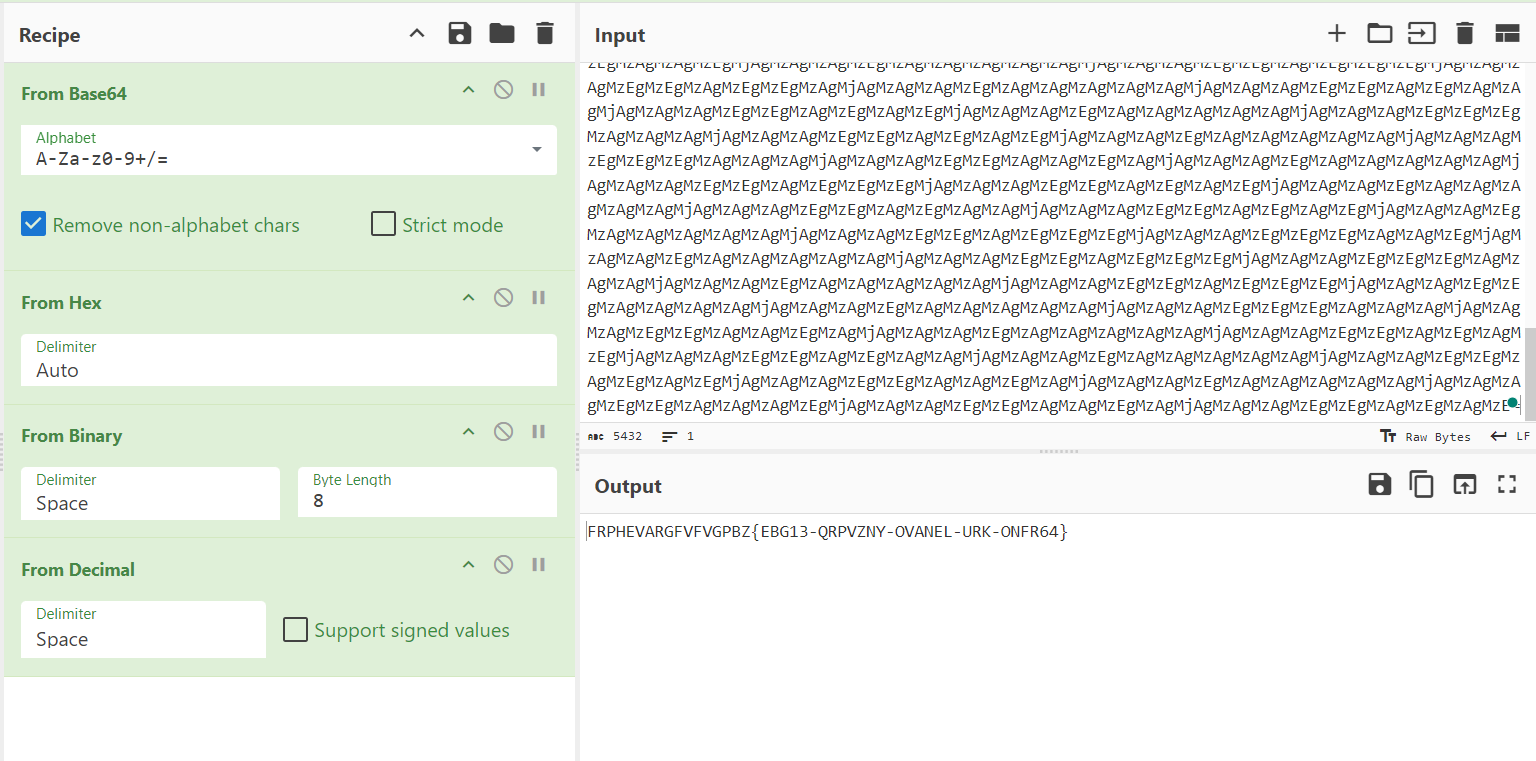
MzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzEgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzEgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzEgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzEgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzEgMzAgMjAgMzAgMzAgMzEgMzAgMzAgMzAgMzAgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzAgMzEgMjAgMzAgMzAgMzEgMzEgMzAgMzAgMzEgMzAgMjAgMzAgMzAgMzEgMzEgMzAgMzEgMzAgMzE=
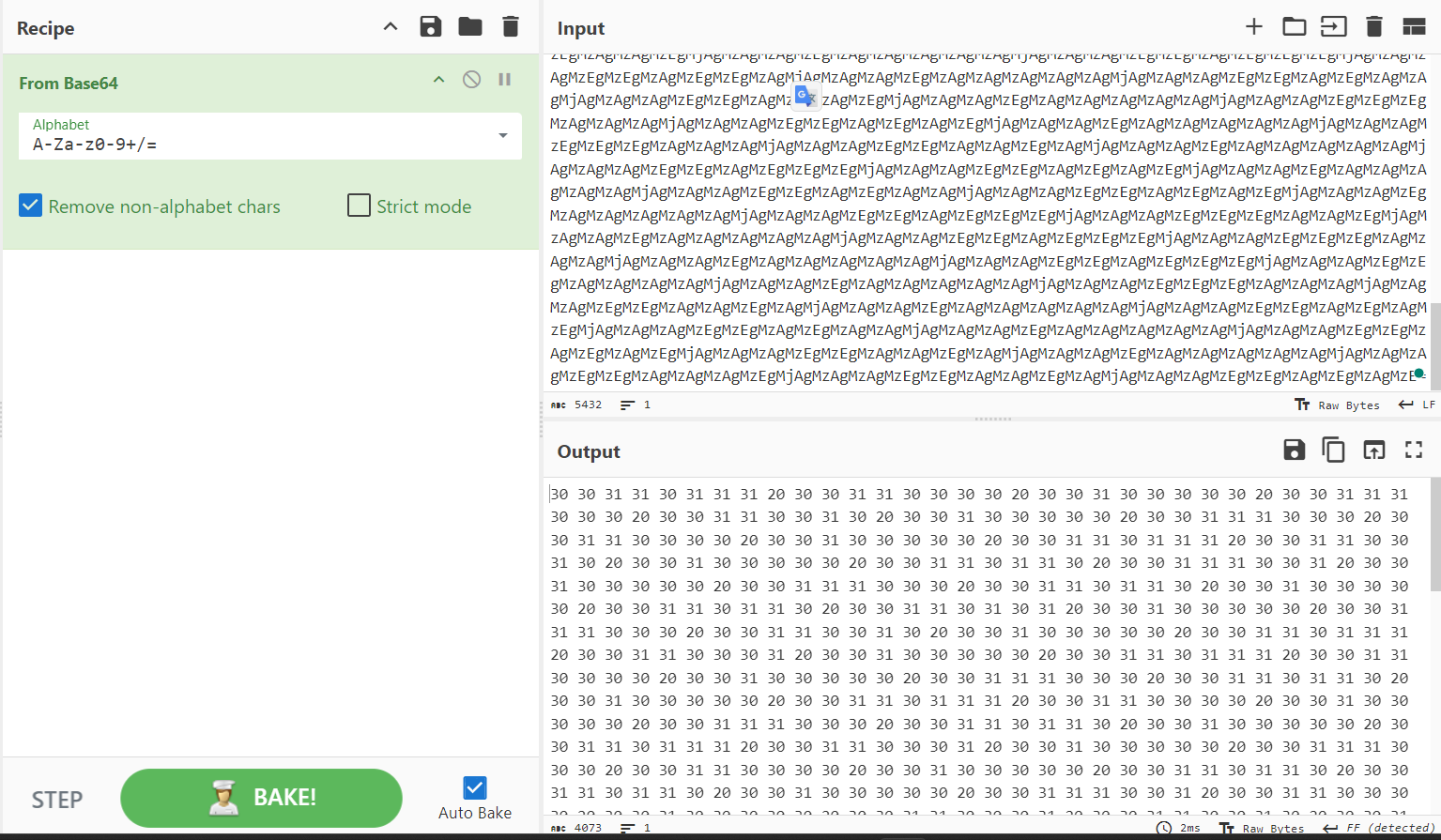
We can see that the flag is encrypted in base64, so let’s visit the CyberChef website to decode it.
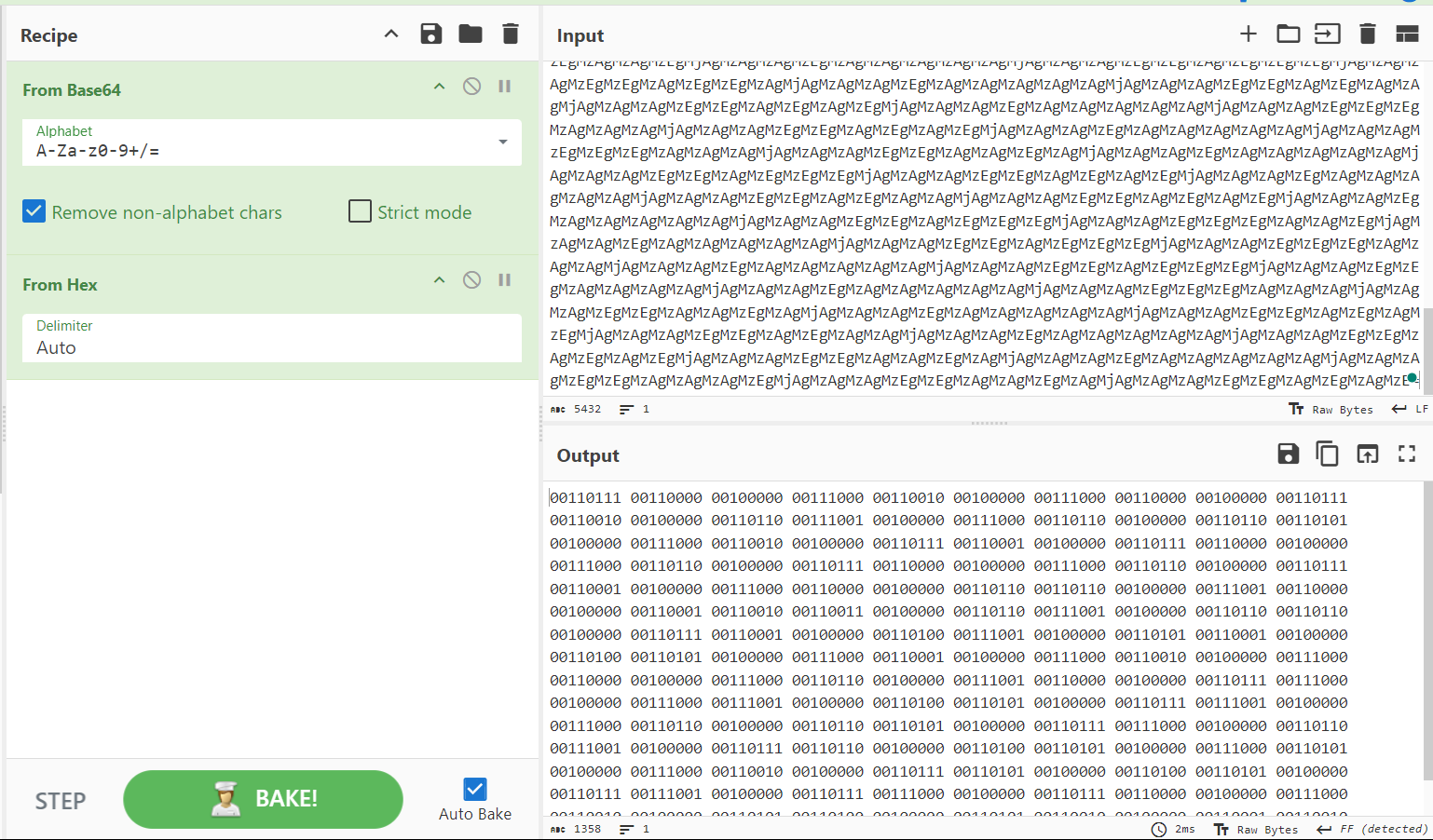
We observe that the output is in hex format, so let’s proceed to decode it.
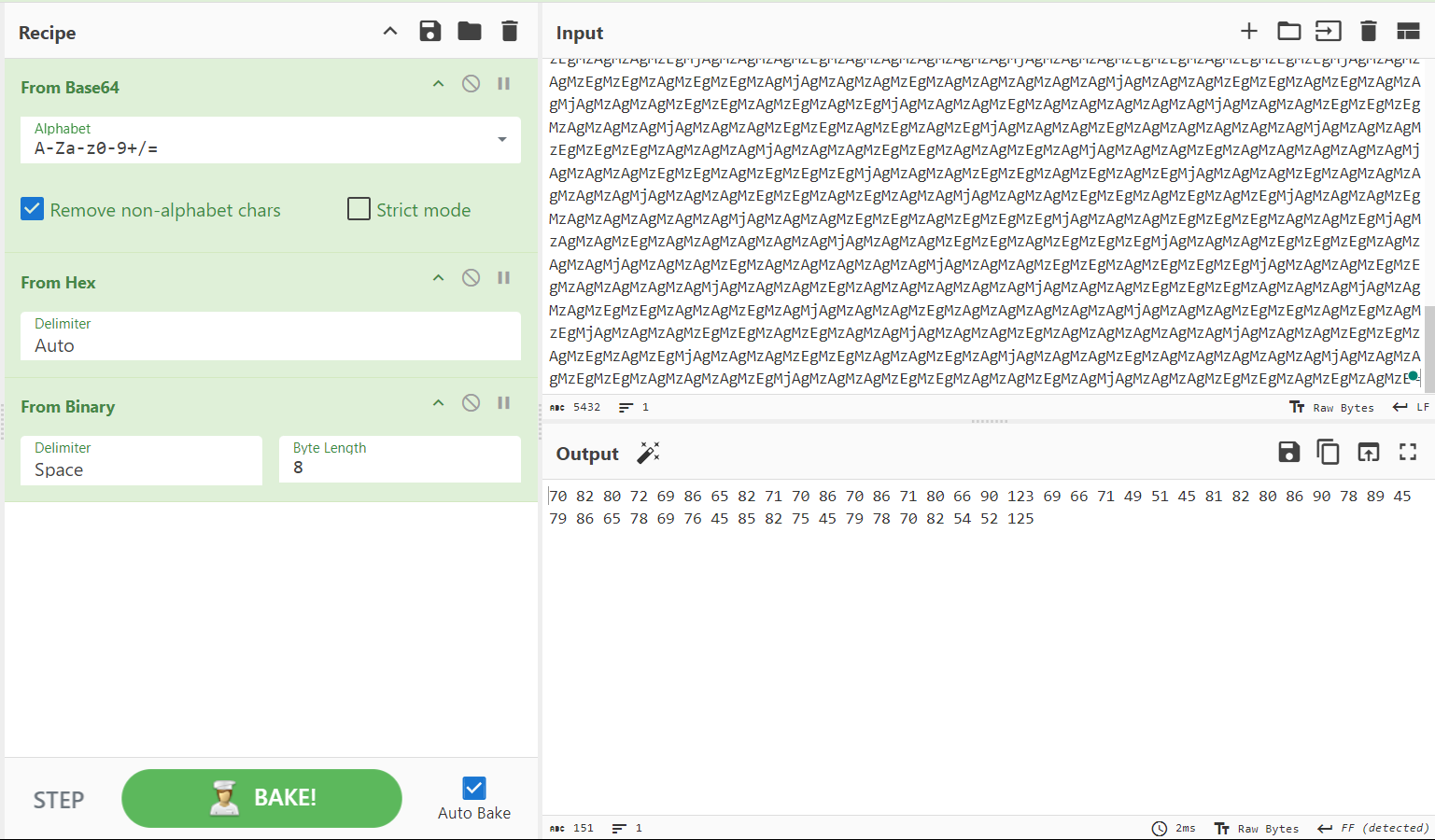
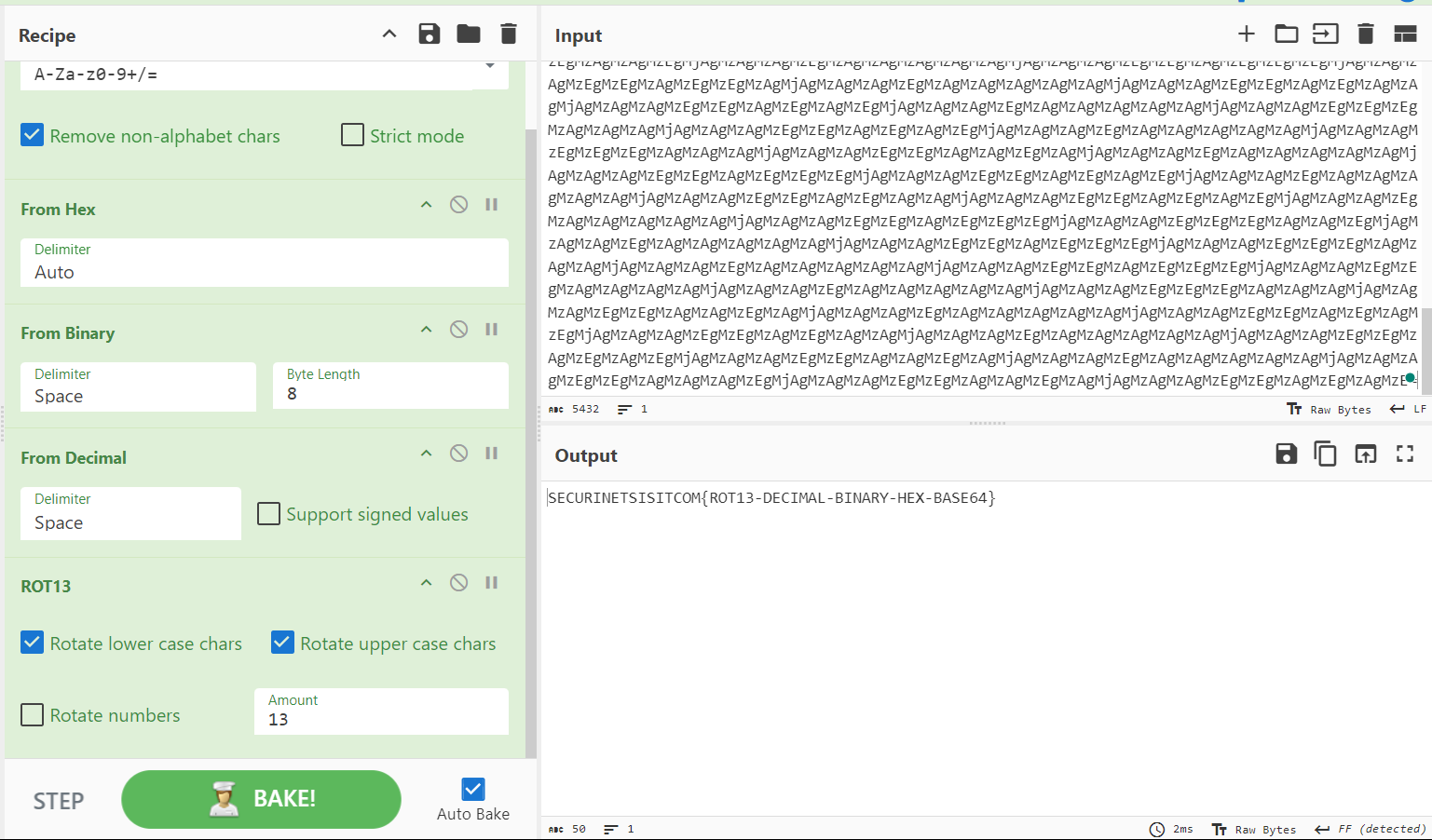
The output is in binary now, so let’s figure out how to decode it.
And now we’ve got a decimal output! Let’s take a moment to decode it together:
Finally, we found our flag, but it was still encrypted. We noticed that the flag consists only of characters without numbers, so I suspect it’s a ROT13 encryption. Let’s try to decode it:
Here is our flag: SECURINETSISITCOM{ROT13-DECIMAL-BINARY-HEX-BASE64}
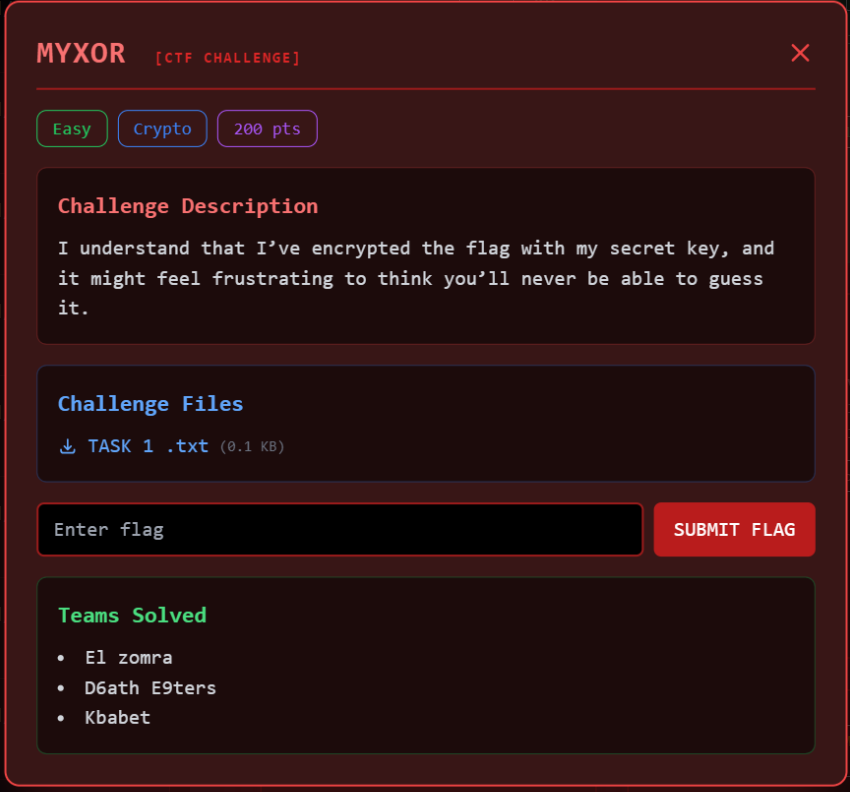
Task 4:
I uploaded this encrypted flag for the challenge, so take a look!
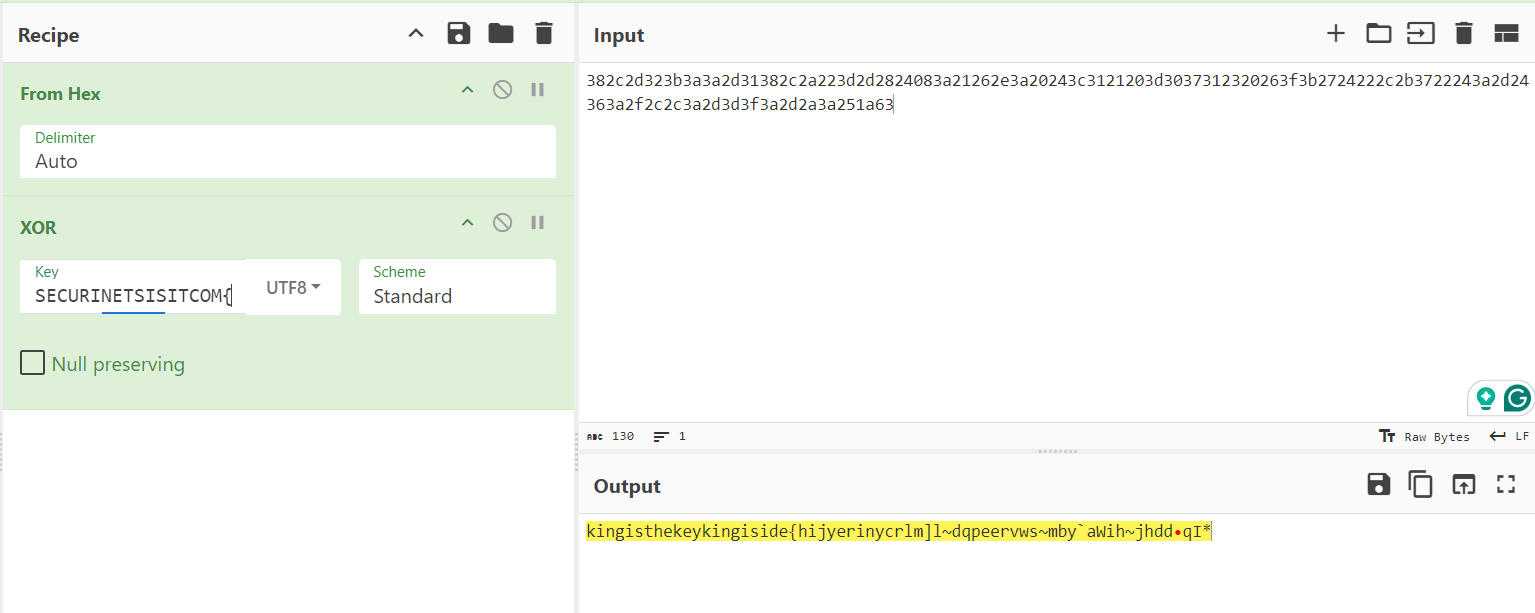
382c2d323b3a3a2d31382c2a223d2d2824083a21262e3a20243c3121203d3037312320263f3b2724222c2b3722243a2d24363a2f2c2c3a2d3d3f3a2d2a3a251a63
HINT: Remember the flag format and how it might help you in this challenge!
We are also given part of the plaintext flag, SECURINETSISITCOM{...}. Using this information, we can deduce part of the encryption key and eventually retrieve the full flag.
Solution Steps:
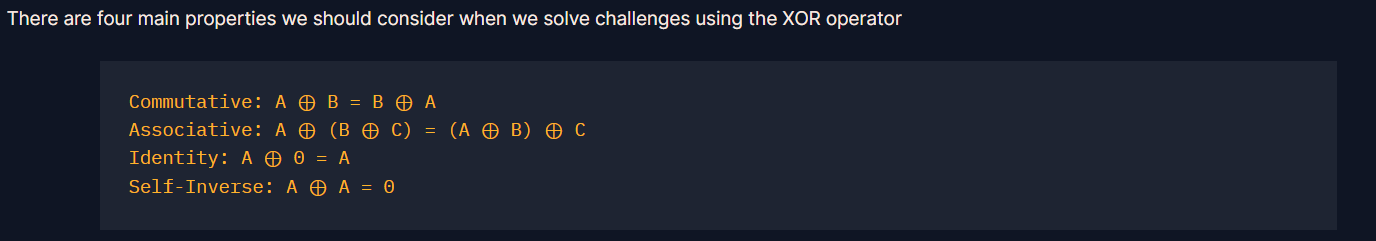
Step 1: Understand the XOR Encryption and don’t forget these properties
This challenge uses XOR encryption, where: Cipher(encFlag) = Flag XOR Key If we know part of the plaintext (Flag), we can deduce part of the key: Key = Cipher XOR Flag
Step 2: Convert the Cipher Text & XOR to Find the Key
The ciphertext is provided in hexadecimal format. First, we decode it for easier manipulation with CyberChef:
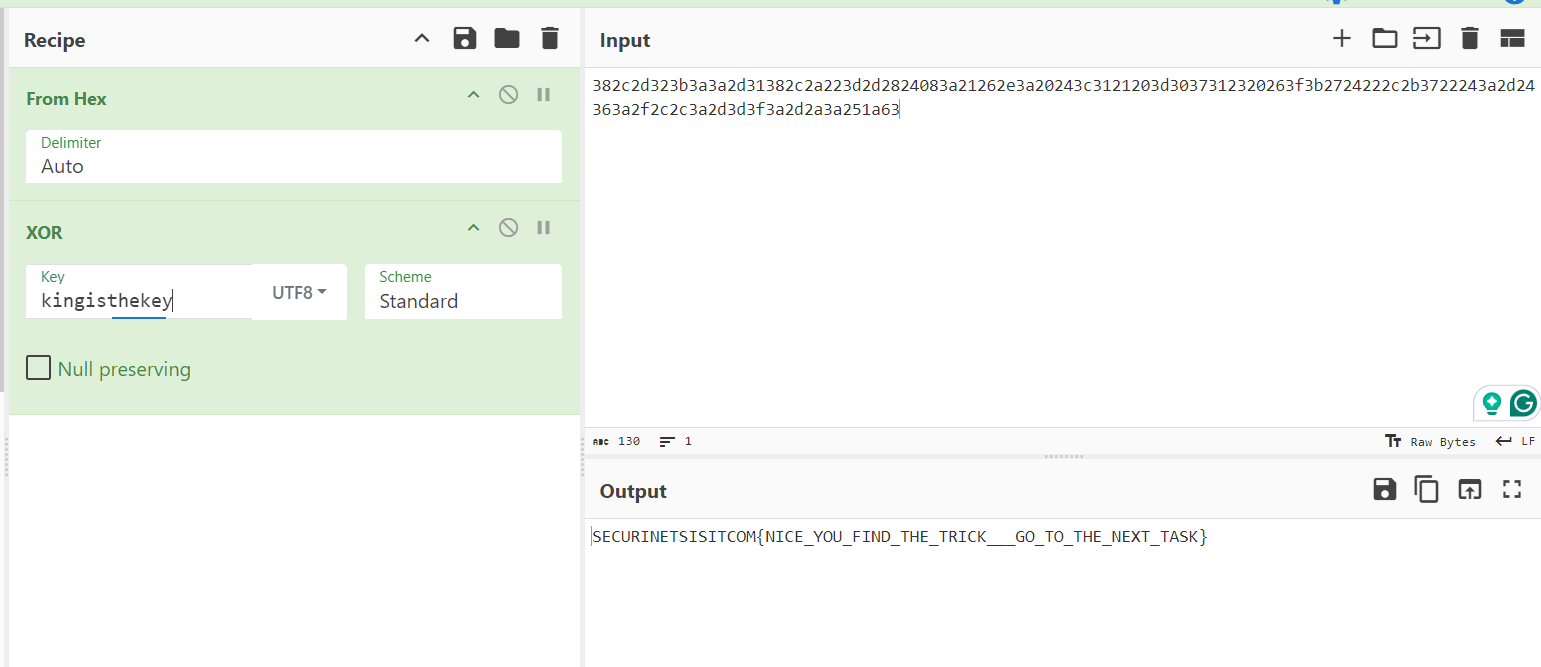
This reveals the key: kingisthekey
So let’s get our flag:
SECURINETSISITCOM{NICE_YOU_FIND_THE_TRICK___GO_TO_THE_NEXT_TASK}
Task 5:
HINT: This challenge requires performing a visual XOR between the RGB bytes of the two images and note that you need to resize the images to decode it
We’re going to create a Python script that will help us perform bitwise XOR operations on images. I typically recommend using the OpenCV library, as it’s a great tool for this kind of work!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
import cv2
# Read two images. The size of both images must be the same.
img1=cv2.imread('hello.png')
img2=cv2.imread('world.jpg')
# Resize the img 2 to have the same size as img 1
img2 = cv2.resize(img2, (img1.shape[1], img1.shape[0]))
#Compute the bitwise XOR on two images using cv2.biwise_xor(img1, img2).
xor_img = cv2.bitwise_xor(img1,img2, mask = None)
#save the image
cv2.imwrite('flag.jpg',xor_img)
Here’s our new XORed image! Let’s go ahead and open it up.
And our flag is SECURINETSISITCOM{XOR_1T_1F_U_C8N}
Task 6:
The attached file has everything you need about the task:
1
2
3
4
N = 18814840635346619874425333469811897321549418263501570889282825750834515074675420955536024872473333925100162290869450343342196370005147241590450746764679485718567750837860298441879336049949463769103929953264633072242523089509554532420960226194229074889893991993272393955287647019173019565996826761031489963195126291001577851134834313095727805927258826762839259238704853071924049305921348548805171136582998855037946513227862183246591156434241274337978149248881248098712196426195343743140711782990404627731190157041047720437406870278036078843043167368486244024032010310184530070850162225094426996919028658409155918085541
e = 0x3
encFlag = 26572349774532122558413822660787565800876859961042748864197505662294319821137420537449406034432755970252620682951620140376826571119571396577525308224469379695704886151366719681917316926664475491403254419941927069176375066837735027264004604420524982390706651874487308796663467648818962491218331170345389279578813057125
It’s interesting to note that this encryption method relies on a small public exponent, 𝑒=3. However, it can be a bit risky because it might be vulnerable to certain attacks, especially if the plaintext message is on the smaller side compared to the modulus N.
So we need to create a python script to exploit the small public exponent vulnerability in RSA encryption. If the plaintext 𝑚 is small enough that 𝑚^𝑒 < 𝑁, the ciphertext c is simply 𝑚^𝑒. The script calculates the e-th root of 𝑐 (here 𝑒 = 0x3 = 3) to recover the plaintext directly, converting it to readable bytes.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
from sympy import root
from Crypto.Util.number import long_to_bytes
# Encrypted flag (ciphertext), modulus (N), and public exponent (e)
encFlag = 26572349774532122558413822660787565800876859961042748864197505662294319821137420537449406034432755970252620682951620140376826571119571396577525308224469379695704886151366719681917316926664475491403254419941927069176375066837735027264004604420524982390706651874487308796663467648818962491218331170345389279578813057125
N = 18814840635346619874425333469811897321549418263501570889282825750834515074675420955536024872473333925100162290869450343342196370005147241590450746764679485718567750837860298441879336049949463769103929953264633072242523089509554532420960226194229074889893991993272393955287647019173019565996826761031489963195126291001577851134834313095727805927258826762839259238704853071924049305921348548805171136582998855037946513227862183246591156434241274337978149248881248098712196426195343743140711782990404627731190157041047720437406870278036078843043167368486244024032010310184530070850162225094426996919028658409155918085541
e = 0x3
# Calculate the cube root of the ciphertext to recover the plaintext (m)
m = int(root(encFlag, e))
# Convert the plaintext (integer) to bytes
plaintext = long_to_bytes(m)
# Print the result
print(plaintext)
Flag: SECURINETSISITCOM{Small_e_Is_Bad_My_Friend!}