Cryptography Writeups - FriendlyCTF 23
Here are my personal writeups for the Cryptography challenges from Securinets FriendlyCTF 2023!
Intro
Whether you’re a beginner or already into CTFs, I hope these solutions help you learn something new or see a different approach.
Description
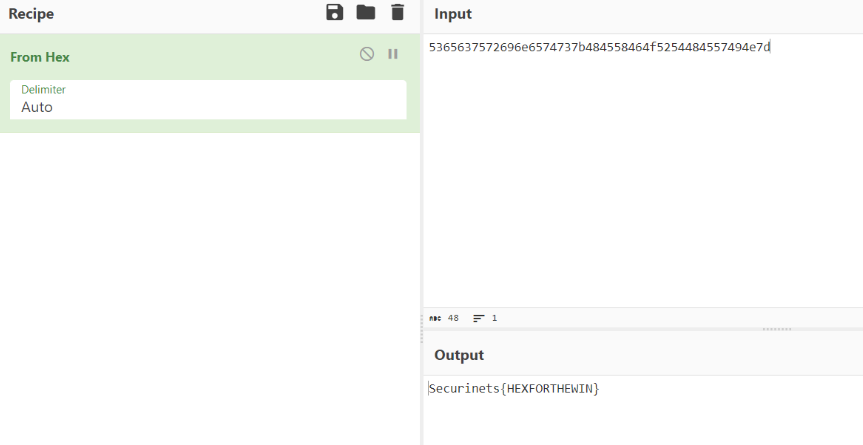
Challenge: Encoding 01
Description: flag=
5365637572696e6574737b484558464f5254484557494e7d
As we can see from the description, the flag is in hex so we need to decode it and we can do this online with CyberChef
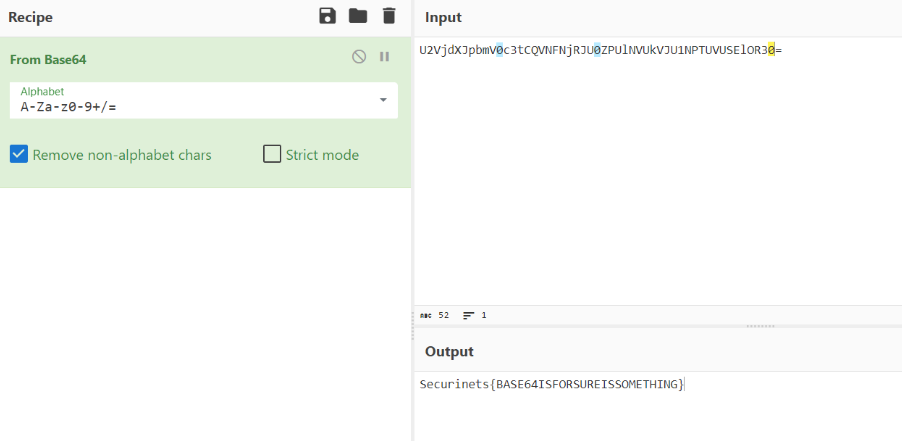
Challenge: Encoding 02
Description: flag=
U2VjdXJpbmV0c3tCQVNFNjRJU0ZPUlNVUkVJU1NPTUVUSElOR30=
Another encoding we don’t need to search for the type because the last char is = which is related to b64
Challenge: Encoding 03
Description:
695831559509425648824083007919730262424152059344495562078194371075772558986882220904478002799741
I guess this a long integer so let’s solve it with Python script:
1
2
3
4
5
6
7
8
9
10
11
12
13
from Crypto.Util.number import long_to_bytes
# Your long integer
long_integer = 695831559509425648824083007919730262424152059344495562078194371075772558986882220904478002799741
# Convert the long integer to a byte string
byte_string = long_to_bytes(long_integer)
# Print the byte string
print(byte_string)
#Output:
b'Securinets{EvrythingIsAnIntegerInTheEnd}'
Challenge: RSA 01
Description:
c=83540897300728379177076501636210631547760510617274853873030211753877608999114p=392964093407393749408017462279326095462187633908223198126587369718012590606979e=7
note that u have p>c so we can use it as the public key n so phi going to be phi = p -1 and m = pow(c,d,p #p_not_n)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
from Crypto.Util.number import long_to_bytes
# m(plaintext) = c^d mod n
p = 392964093407393749408017462279326095462187633908223198126587369718012590606979
c = 83540897300728379177076501636210631547760510617274853873030211753877608999114
e = 7
phi =p-1
d = pow(e, -1, phi)
m = pow(c,d,p)
print(long_to_bytes(m))
#Output:
b'Securients{RSA_IS_THE_BEGGINING}'
Challenge: RSA 02
Description:
n=16216224378176880528983105151997907926681888078389463921750042927430841618003058575861018336213144417863329427348404906981059892079378789074226040552355228450002542279035612988442317309011173942719556883100041246497937525703148797372051587599496825848069327409679715214296936604752020668600994362294011464823391877606846343943733922202230172851350341934665586496653738310061787859007026725451903598019097606327043736016882464416317388001708591979279911488416922551705609304211766550282228344616794294013834171905744283131204289774901897590317456828571173531980844283601336423867969316962394201175015357570898195683817e =3encFlag =40378828974014904250461375751142777486518879329128357181278373939048875002629003832270237799217838353922025116225310438390910853151517964146147890063077612454969002380184688399313145194821409125
1
2
3
4
5
6
7
8
9
10
11
12
13
14
from sympy import root, Mod
from Crypto.Util.number import long_to_bytes
c = 40378828974014904250461375751142777486518879329128357181278373939048875002629003832270237799217838353922025116225310438390910853151517964146147890063077612454969002380184688399313145194821409125
n = 16216224378176880528983105151997907926681888078389463921750042927430841618003058575861018336213144417863329427348404906981059892079378789074226040552355228450002542279035612988442317309011173942719556883100041246497937525703148797372051587599496825848069327409679715214296936604752020668600994362294011464823391877606846343943733922202230172851350341934665586496653738310061787859007026725451903598019097606327043736016882464416317388001708591979279911488416922551705609304211766550282228344616794294013834171905744283131204289774901897590317456828571173531980844283601336423867969316962394201175015357570898195683817
m = int(root(c, 3))
plaintext = m % n
print(long_to_bytes(plaintext))
#Output:
b'Securinets{bigNSmalleIsBad}'
Challenge: RSA 03
Description:
pubkey= 7445032506702760330480990020950608660488544145501396616695107193222769110126474966949204137860702423042393448253263507548369759909724431567968359596424941 p= 90740000887009928802975523427929382290530933051305995241083293620231779189057q= 82047965989920650863263349526788234428066500046758922974929509944594959869613e= 65537ciphertext= 5975023360621335519748698669649125733282218902243127291304081681695121681394044871008421583534587011333598278310154111230904696933558313388360031158271221
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
from Crypto.Util.number import long_to_bytes
# m(plaintext) = c^d mod n
p = 90740000887009928802975523427929382290530933051305995241083293620231779189057
c = 5975023360621335519748698669649125733282218902243127291304081681695121681394044871008421583534587011333598278310154111230904696933558313388360031158271221
n = 7445032506702760330480990020950608660488544145501396616695107193222769110126474966949204137860702423042393448253263507548369759909724431567968359596424941
e = 65537
q = 82047965989920650863263349526788234428066500046758922974929509944594959869613
phi = (p-1)*(q-1)
d = pow(e, -1, phi)
m = pow(c,d,n)
print(long_to_bytes(m))
#Output:
b'Securinets{RSADECRYTION}'
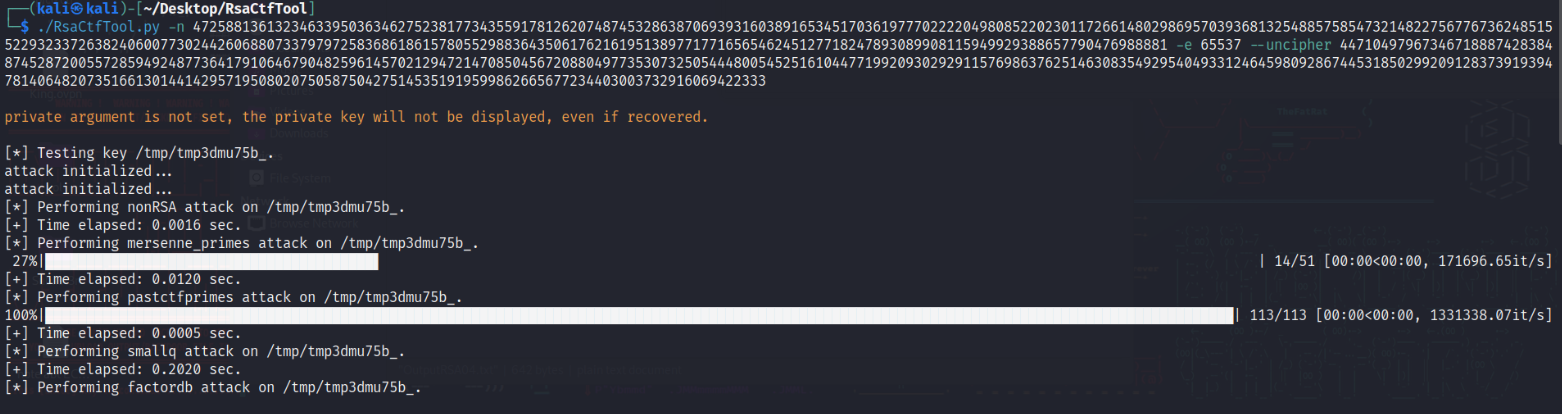
Challenge: RSA 04
Description:
n=47258813613234633950363462752381773435591781262074874532863870693931603891653451703619777022220498085220230117266148029869570393681325488575854732148227567767362485155229323372638240600773024426068807337979725836861861578055298836435061762161951389771771656546245127718247893089908115949929388657790476988881e =65537encFlag =44710497967346718887428384874528720055728594924877364179106467904825961457021294721470850456720880497735307325054448005452516104477199209302929115769863762514630835492954049331246459809286744531850299209128373919394781406482073516613014414295719508020750587504275145351919599862665677234403003732916069422333
for this challenge we’ll be solving it in two ways the first is going to use RsaCtfTool
and the second is u can use this website to factorize the n value and get p and q and use Python script to get the flag
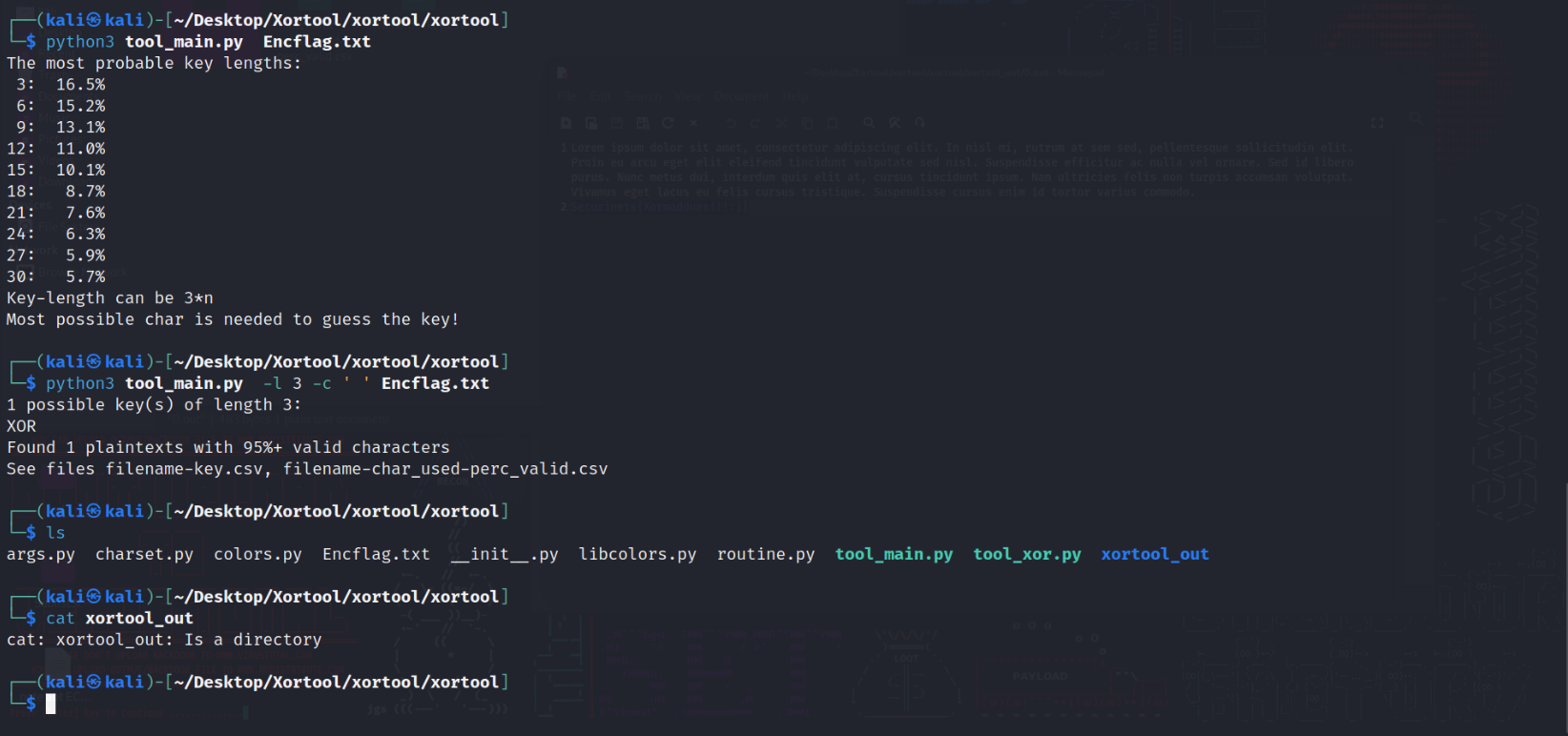
Challenge: XorMadness
Description: This task contains two files the encflag and the source code:
Encflag = � ="r1?!-"r< >7=r+&&x.?=;~x,=6<7;;7,: x.61?;+,;6(r=#;,ar�!r6&!4o?1cr*:&:?x.&x<75o!=+~x?74#76;7+>'=o!7#>1,;,:61!r=#;,ar�==1!r=:r9=1-o7?&x*>1;r=#71)76+r,&<;&6-!&x9'4?',.&=o!=+r6&!4ar :!(<<&!+r=)41,;,: x.1x!'4#3x974o=!3**|x�7<o;1-7 r(: -<|x�'6,r5*&-<r<:;to;6;7*+'5o#-&!x*>1;r9;~x,'<'+o&1!11+'6;r1?!-"|x�35o'4; 1,;=>1<r6 <x;'?;+o3;,'5<36o$7#',?3,ar�&$9"'+o7?&x#3;:!x*'x)74&!x,'<'+o&&!,&#-|x�'+?76+;+<7x,'<'+o76&?x&6x;=*;=o$9=;-<r; ?5 67aX 1-=;6&+4 7=?9+66!ynsbf/
1
2
3
4
5
from pwn import xor
flag="Lorem ipsum dolor sit amet, consectetur adipiscing elit. In nisl mi, rutrum at sem sed, pellentesque sollicitudin elit. Proin eu arcu eget elit eleifend tincidunt vulputate sed nisl. Suspendisse efficitur ac nulla vel ornare. Sed id libero purus. Nunc metus dui, interdum quis elit at, cursus tincidunt ipsum. Nam ultricies felis non turpis accumsan volutpat. Vivamus eget lacus eu felis cursus tristique. Suspendisse cursus enim id tortor varius commodo.\n"+"Securinets{this_isfakeflag}"
key="????????????"
encFlag=xor(flag,key)
open("Encflag.txt","wb").write(encFlag)
I have used Xortool tool to solve it as shown below:
and here we have our flag: Securinets{Xormaddnes!!!:)}