TryHackMe: Net Sec Challenge – Walkthrough
This post is a walkthrough of the Net Sec Challenge room on TryHackMe, a great lab to sharpen your network security skills.
Desciption
🧠 TryHackMe Difficulty Rating: Medium
📁 Room Type: VIP
The challenge covers practical use of tools like:
nmapfor network scanning,telnetfor remote access,- and
hydrafor brute-force attacks.
In this writeup, I walk through each step of the exploitation process, from initial enumeration to final access. Whether you’re preparing for a CTF or just want to level up your recon skills, this challenge is worth a try!
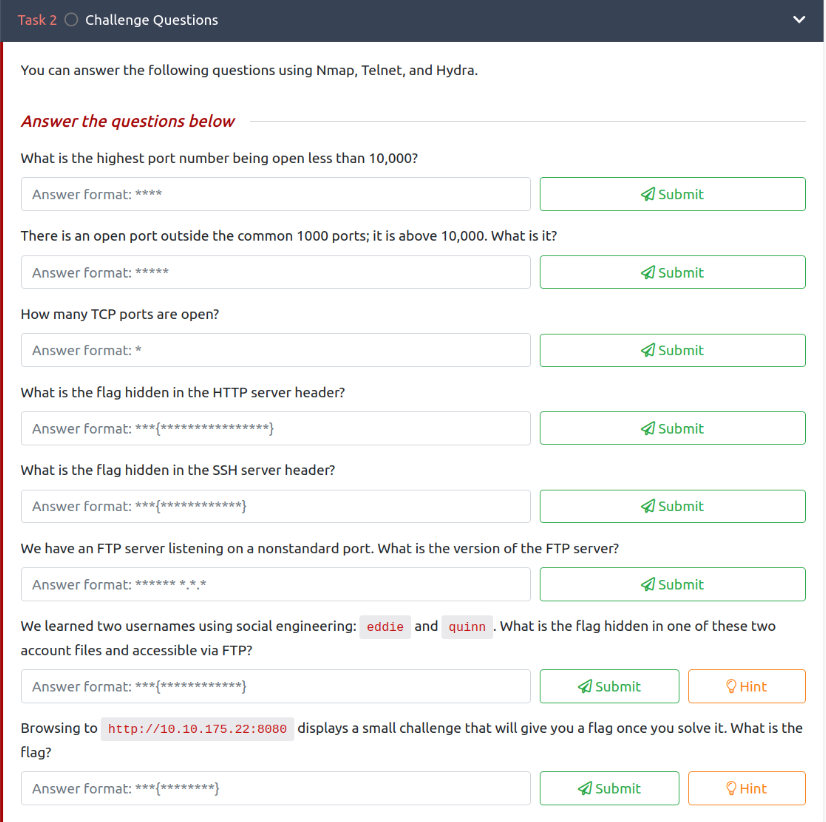
Task 1: Introduction Task 2: Challenge Questions
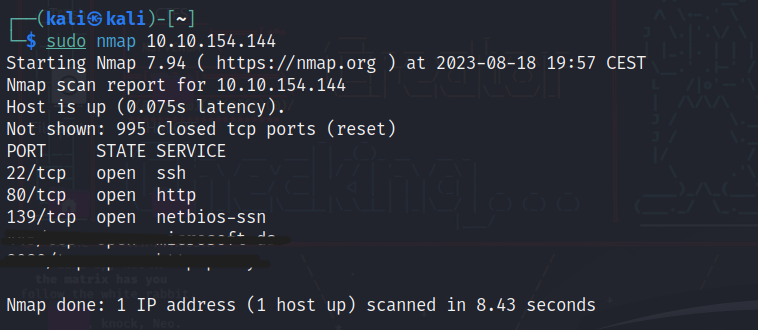
Q1: What is the highest port number being open less than 10,000?
We are going to use Nmap to scan our target machine for open ports with this command: $ sudo nmap MACHINE_IP
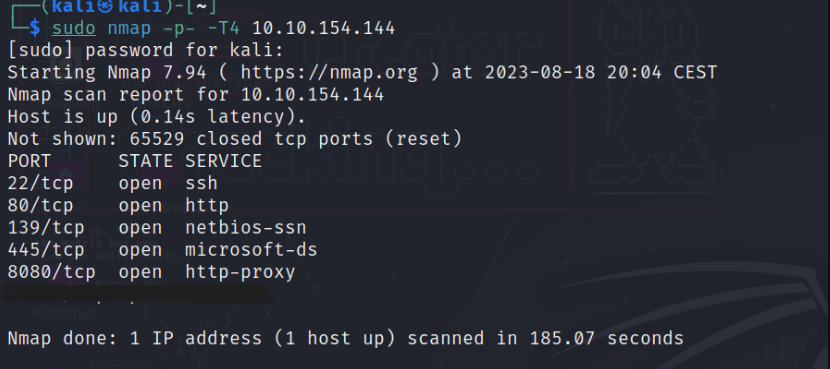
Q2 + Q3: We need now to scan for all the ports to be able to answer these questions. As a result, the scan may take several minutes or more.
Our is command: $ sudo nmap -p- -T4 MACHINE_IP -v (where -p-:scans all the ports, -T4: for faster scan and -v: for verbose)
Q4 + Q5: we need to use this command
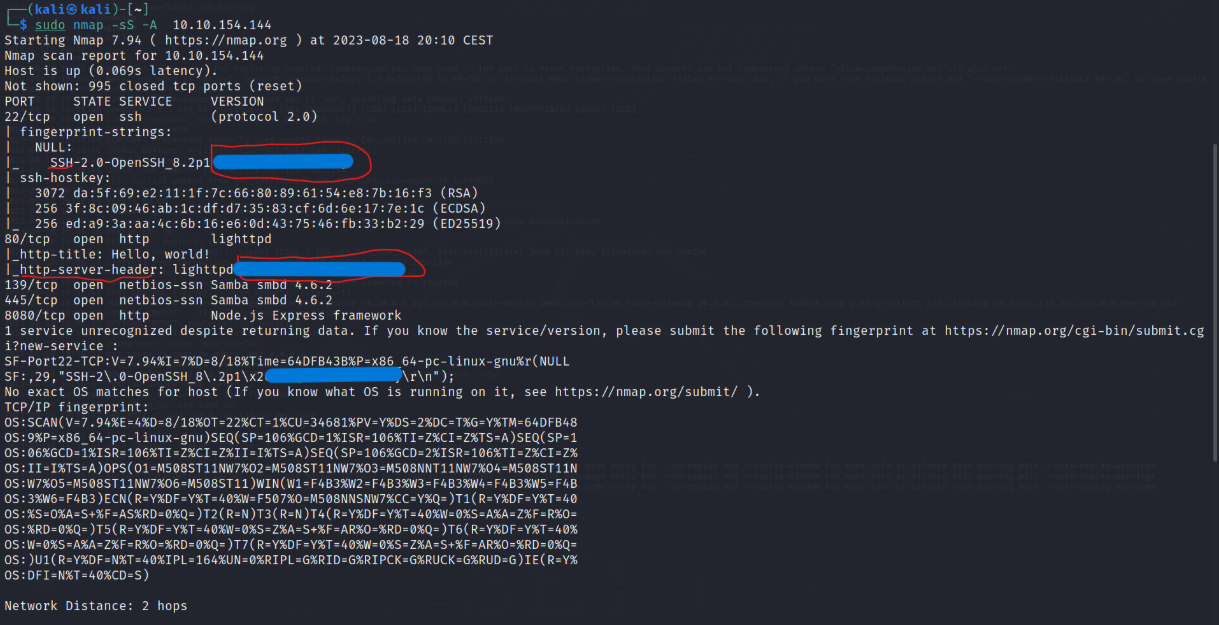
$ sudo nmap -sS -A MACHINE_IP(where-sS: for TCP SYN Scan and-A: eq to-sV -O -sC --traceroutewhere-sV: determine service/version info on open ports,-O: detect OS,-sC: run default scripts and--traceroute: run traceroute to target)
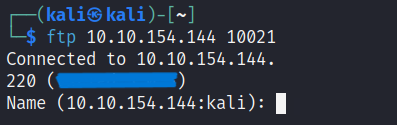
Q6: we know that the FTP server is listening on a nonstandard port Port 21 is wrong so I tried port number 10021 which has an unknown service
Our command is : $ ftp 10.10.154.144 10021
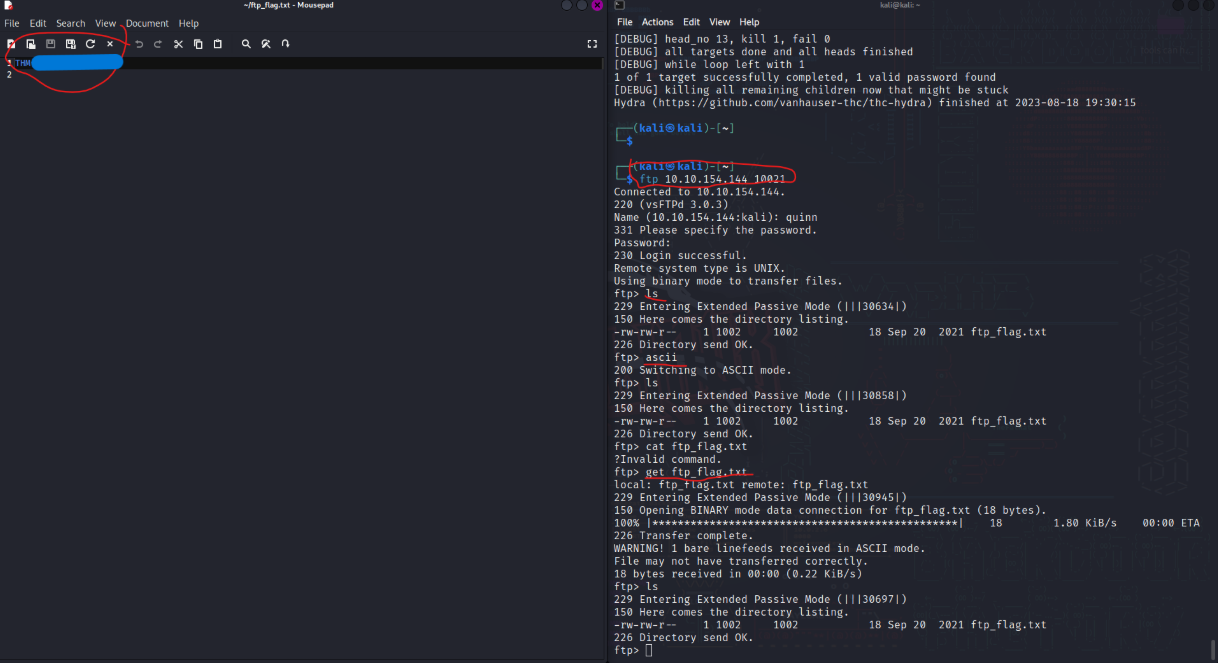
Q7: We learned two usernames using social engineering: eddie and quinn. To get the flag hidden in one of these two account files, first of all, we need to save these usernames to a file. Then we will use Hydra and
/usr/share/wordlists/rockyou.txtfile to figure out their passwords.
step 1: $ hydra -l eddie -P /usr/share/wordlists/rockyou.txt 10.10.154.144 ftp -vV -d -s10021 (to find the pass of eddie)
step 2: $ hydra -l quinn -P /usr/share/wordlists/rockyou.txt 10.10.154.144 ftp -vV -d -s10021 (to find the pass of quinn)
-l: Provide the login name-P: Loads several passwords from a file-vV: Show the username and password combinations being tried-d: Debugging the output-s: For specific port
After finding the passwords we need to connect and get the flag:
Q8: To answer the last question of the challenge we need to visit
http://MACHINE_IP:8080.
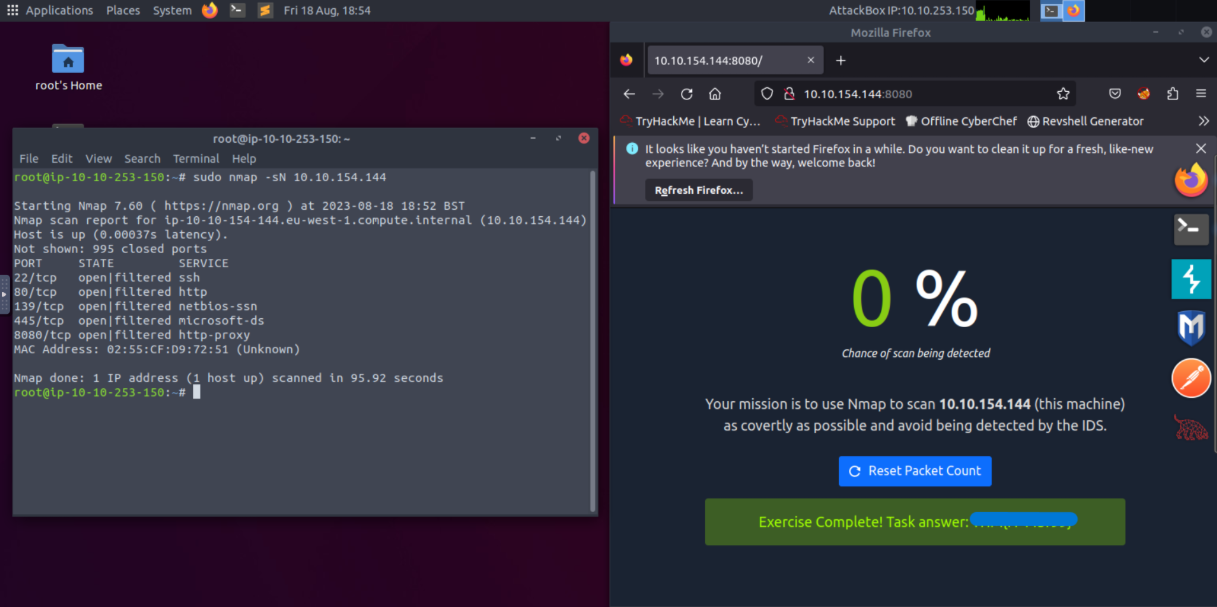
To reduce the probability of being detected, we are going to run a NULL scan using Nmap. As you might remember, the null scan does not set any flag. And by sending requests which do not include the SYN flag, we can bypass the firewall.
Our command is : $ sudo nmap -sN MACHINE_IP (-sN: for Null Scan)
The flag appeared instantly after I hit enter to run the scan. Task completed 🙂
Note: If it doesn’t work from your local machine, try running nmap on the AttackBox. :
I hope this write-up helped you to complete this challenge
!! HAPPY LEARNING !!